Introduction Have you ever opened an Excel file and realized that some sheets are locked with a…
Ethical Hacking
5 Articles in this Category
Step-by-step ethical hacking guides, focusing on responsible information gathering and security testing methods.
Overview Fire Ant is an advanced cyber-espionage campaign targeting VMware vSphere environments (vCenter, ESXi) and adjacent appliances…
Running applications on Windows often requires administrator privileges, especially during installation. However, there’s a lesser-known workaround using…
Introduction: Google Dorking is a technique that allows ethical hackers, system administrators, and cybersecurity professionals to uncover…
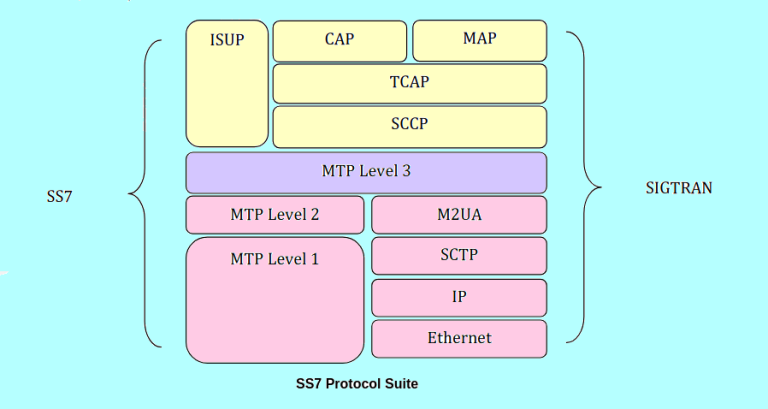
I’m excited to share this thought-provoking video by Veritasium, which explores the vulnerabilities in our phone networks…